
Forensic intelligence analysis of counterfeit banknotes in the ‚Äúglobal and digital‚ÄĚ age
12.08.2016BACKGROUND
Martin F√ľrbach‚Äôs main areas of expertise as a questioned document expert are the forensic aspects of counterfeiting by traditional and digital printing techniques, forensic analysis of inkjet printers and paper analysis. His PhD research deals with the systematic application of image and metrical analysis to the forensic intelligence of counterfeit banknotes and documents. As a hobby, he is interested in historical research that focuses on state-supported counterfeiting, mainly the counterfeiting of British Pounds during Operation Bernhard in Germany (1942-1945).
Types of examination
The term ‚Äúcounterfeit examination‚ÄĚ does not properly describe the process or its main aim. Depending on the context, people and institutions involved, the aim of counterfeit examination can be divided into three different categories.
The initial examination of the suspicious banknotes starts with a determination of their authenticity, i.e. it is determined whether are genuine or counterfeit. In the majority of cases this can be done by comparing the printing techniques, the characteristics of the paper and examining the security features to those of the specimen (which is an authentic note used as reference). In the case of digital counterfeits, this determination can be done with a categorical conclusion even without physically possessing a reference specimen. Multiple companies offer currency databases, and with the assistance of their detailed descriptions and images of banknotes in various light conditions, experts can conclude whether the note in question is indeed counterfeit. For example, the simple knowledge that a genuine banknote is printed through a combination of offset, intaglio and letterpress on security watermark paper allows experts to identify a counterfeit if it is printed on commercial office paper using inkjet technology.
However, experts should exercise caution when reaching the inverse conclusion that the suspect note is genuine. This should be based on a deeper analysis than the simple observation that there are no obvious differences; otherwise, it is risky to conclude that the note in question must be genuine because it was printed using the same techniques as reference specimen. There are numerous examples where conclusions of authenticity that were based only on this observation have been wrong ‚Äď from the ‚ÄúOperation Bernhard‚ÄĚ counterfeits (British pounds counterfeited in Germany during WWII) to high-quality counterfeits of US dollars, the so-called superdollar.
Nevertheless, it is improper to use the term ‚Äúcounterfeit analysis‚ÄĚ (or ‚Äúexamination of counterfeit banknote‚ÄĚ) to describe above mentioned stage of the analysis because it indicates possible conclusion of expertise. Instead, those objects under examination should be referred to as ‚Äúbanknotes in question‚ÄĚ or ‚Äúquestioned (suspect) banknotes‚ÄĚ instead of ‚Äúcounterfeit‚ÄĚ as their status has yet to be conclusively determined.
The second type of examination of suspect notes (determined as counterfeits) can be characterized as forensic intelligence analysis. This is done with the main objective of determining if multiple counterfeits share the same source or not (i.e. whether they came from one counterfeiter). Particularly with regard to digital counterfeiting, it is important to determine if the counterfeiting is being done on a small scale by occasional counterfeiters or by experienced counterfeiters. Various information can be evaluated from the technical document examination of the counterfeits to other forensic evidence such as fingerprints, the modus operandi of entering the notes into circulation, geographic and time analysis indicating patterns in the behaviour of the person entering the notes into circulation, etc. Forensic intelligence analysis is the main subject of this article.
The third type of examination is an evaluation of the value of the evidence. When a suspect is found and materials and devices are seized, police or judicial authorities then require experts to determine if the seized materials were used for the production of the counterfeits in question. Contrary to the forensic intelligence that may produce links even when real links do not exist, evidence evaluators have to avoid making errors of this type (i.e. they must not conclude that the counterfeits originated from the seized materials if in fact they do not).
How does the forensic intelligence approach work?
The forensic intelligence approach to the counterfeiting of banknotes is based on the following premises:
· A particular counterfeiter produces the same type of counterfeits in the same quality (intra-variability is very low). This allows counterfeits from one counterfeiter to be linked together according to their shared characteristics.
· Different counterfeiters produce counterfeits differently. The counterfeits produced by Counterfeiter 1 are different from the counterfeits produced by Counterfeiters 2, 3,…n (inter-variability is ideally very high) (Fig. 1).
Counterfeits that are seized or entered into circulation can be easily classified into particular classes (and those classes correspond to the counterfeiters) (Fig. 2).
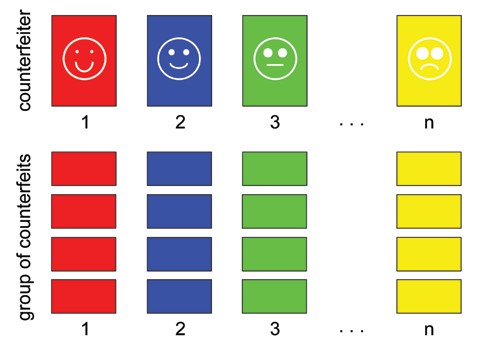
Fig. 1. Illustration of classes of the counterfeits. Counterfeiter 1 produces class of counterfeits 1, that is different from counterfeits in classes 2, 3, … n, that are produced by Counterfeiters 2, 3…n (to signify the classes of counterfeits from the same counterfeiter, the same colour is used).
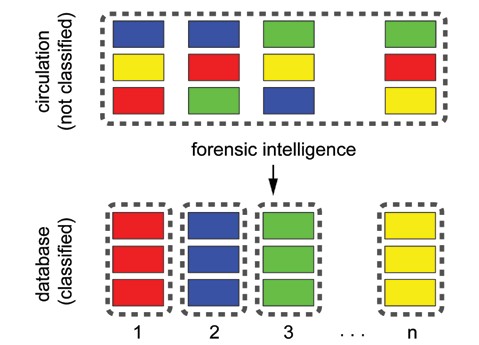
Fig. 2. Effective forensic intelligence analysis will create different classes of counterfeits ( to signify one class of counterfeits, the same colour is used).
Unfortunately, the majority of counterfeits are not signed by their counterfeiter and bear neither his DNA nor his fingerprint. Instead, the features identifying the counterfeiter are not ‚Äúdirectly‚ÄĚ linked with him. This decreases evidentiary value as most of the valuable forensic evidence link the perpetrator directly to the objects. However, counterfeits that have entered circulation and those that have been contaminated by other people are not ideal substrate for later fingerprint or DNA recovery. For the purposes of the ‚Äúpractical‚ÄĚ forensic intelligence approach, the characteristics of the counterfeiter (as illustrated on Fig. 1) need to be ‚Äúreplaced‚ÄĚ by characteristics that are available for examination by an expert using a questioned document examination. This can be done by considering, for example, the printing technique. Those classes of counterfeits are based on the characteristics of the printers. Printer 1 produces a class of counterfeits 1 that is different from counterfeits produced by Printers 2, 3‚Ķn.
In real cases, counterfeits will not differ only according to their printing techniques, but also according to their many other features ‚Äď the paper, the imitation of security features, presence of defects, etc. Ideally, counterfeits from one group will have unique characteristics that are different from the characteristics of the counterfeits in other groups (Fig. 3). The characteristics of each counterfeit can be described as a combination of the printing technique, the type of paper used, the way the holograms have been imitated, etc. For example, we can characterise ‚Äú–°ounterfeit 001‚ÄĚ as ‚Äúinkjet printed, printed using pigment, paper UV dull, imitation of security feature A‚Ķ‚ÄĚ and so on. These characteristics found can be entered into a database and used to search the next occurrence of the same type of counterfeit.
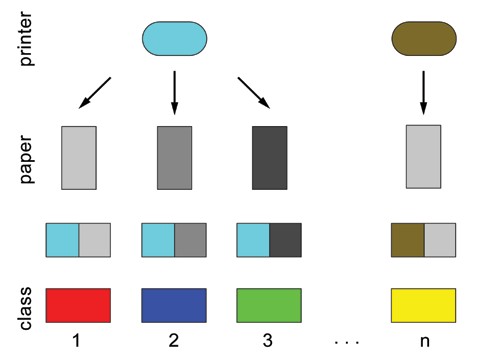
Fig. 3. Classification of counterfeits based on combination of features ‚Äď counterfeits printed on the same printer can be distinguished by the use of different paper.
This approach (and its various modifications) has been used for decades by many central banks and police units and has not significantly evolved. The advantage of this approach is that it is simple, but on the downside, it is rather subjective. Why is this approach being challenged now more than ever before? One of the main reasons is the increase in the presence of ‚Äúdigital counterfeiters‚ÄĚ.
Therefore, a detailed analysis of the current approach is needed. The approach mentioned above works perfectly if:
· The modus operandi of the production of counterfeits is sophisticated
· A high number of security features is imitated
¬∑ The acquisition (and eventual reorigination) of the image is taken from a unique banknote and by a unique modus operandi ‚Äď independently from other counterfeiters
· The market offers large possibilities that the imitation of the security features of those counterfeits produced by Counterfeiter 1 will have unique characteristics and will be different from the characteristics of the counterfeits produced by Counterfeiters 2, 3...n.
· The counterfeiter does not change materials or devices
· The production from one counterfeiter is stable - producing the same quality of counterfeits and imitating the same quantity of security features
· The devices produce the same output during their lifespan
· The counterfeiter produces only one type of currency and from this currency only one nominal value
· All useful forensic intelligence features are discovered and classified in a database (and this is done in reasonable time)
· The methods used for the extraction of the features are as simple as possible
The statements mentioned in the list above are more applicable to counterfeiters from the 1980s than they are to current ‚Äúdigital counterfeiters‚ÄĚ. Previously, there was a limited community of professional counterfeiters and a priori existing links were already high. As conventional machines were expensive and had long lifespans, counterfeiters did not regularly replace them. The forensic intelligence was more effective because of the smaller number of counterfeiters producing for a longer period of time ‚Äďit was also more meaningful to employ surveillance teams or eavesdrop on their communication. Contrastingly, a large number of amateur counterfeiters has led to (the often wrong) a priori belief that ‚Äúthis is an individual case and the chance that it is linked to others is low‚ÄĚ. However, the reality in many countries shows that amateurs and advanced ‚Äúdigital‚ÄĚ counterfeiters are able to produce from dozens to hundreds of counterfeits.
Therefore, the approach described above can be less effective if:
¬∑ The modus operandi of different counterfeiters is very similar ‚Äď the majority of counterfeits are produced in almost the same way (inkjet printing on ‚Äúnormal‚ÄĚ office paper).
· The low number of security features is imitated.
· Sharing of source images takes place.
¬∑ The market for the imitation of security features is rather limited and does not allow each counterfeiter to ‚Äúcreate‚ÄĚ unique combinations of material characteristics.
· Counterfeiters can completely change devices and/or materials as new devices become cheaper.
¬∑ Counterfeiters can develop their modus operandi of production in two opposite directions. They may become more ‚Äúlazy‚ÄĚ (they realise that the security features that they have imitated are not verified and are not imitating those features anymore). Or, the counterfeiter produces for a longer time, as in all other skills, by experience, training and trials and errors become more advanced. In addition, their ‚Äúeducation‚ÄĚ gained with the aid of the Internet can increase their knowledge and the security features not imitated during the beginning of their career might be imitated later as their work qualitatively improves.
· Devices, due to wear, malfunction and shortage of inks can produce different results; for example, a printer’s defect is not visible on counterfeits done at the beginning of the lifespan of the printer but it becomes more visible over time.
· Counterfeiters produce different nominal values and different currencies.
· In practical casework it can be very difficult to determine which features need to be classified, and in some cases they are not discovered at all or they are not evaluated as either important or descriptive.
· Academic research proposes mainly complicated methods of identification based on mass spectrometry, isotope analysis, use of cyclotrons, etc. while completely ignoring the advantages and potential of image analysis methods.
What complicates the process of forensic intelligence analysis is that small differences exist even in counterfeits printed on one device and by one counterfeiter (Fig. 4). Those slightly different colours should be in one class according basic colour, however too sensitive evaluation can form smaller groups. Colour shift was chosen as an illustrative example because it can happen even in actuality - for example, one cartridge colour is at the end of its life and each printout will contain less ink of one colour and the overall colour (composed from four basic colours) will be different and change slightly from one counterfeit to the next. A similar result can be observed due to the different storage conditions of the counterfeits ‚Äď for example, those that are left in direct sunlight fade. Other examples of small differences can be defective printers, leading to the presence of more visible marks on the printouts or latent code with day and time stamps, or examples of counterfeits with similar but different configurations of ‚Äúyellow dots‚ÄĚ (Fig. 5, 5-1).
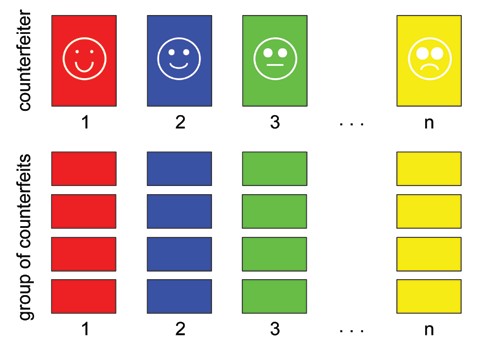
Fig 4. Illustration of small differences between counterfeits from one counterfeiter (different shade of one pure is chosen to represent small differences).


Fig. 5. Practical example of small differences in latent code ‚Äď simple comparison of patterns can lead to the incorrect conclusion that the printers were different. In reality, the printer is the same, only the first counterfeit (left) was printed about one hour before the second one (right).

Fig. 5-1. Code from counterfeit 1 (left above) is represented by magenta, code from counterfeit 2 (right above) ‚Äď by cyan. Difference between codes are marked in the right part of the image.
The approach that enables counterfeits to be linked from the same group, the ‚Äúsame type of colour‚ÄĚ should be ‚Äútolerable‚ÄĚ in small variations and not classify counterfeits as different according those tiny details.
The aim of forensic intelligence analysis can be described as follows:
· All counterfeits having the same origin are linked to proper groups according to their origin
· There are no false positives (counterfeits that do not have the same origin but are [wrongly] linked)
· There are no false negatives (counterfeits that have the same origin but are [wrongly] not linked)
The ideal is when all counterfeits have been properly linked. In reality though, forensic intelligence is a compromise between the two extremes and the ideal state can only be approached from one direction or the other. The first extreme is when the forensic intelligence characteristic chosen was too general and those linking all the counterfeits ‚Äď for example, all the counterfeits of a particular currency and of a particular nominal value. The second extreme considers a small variation in size due to manual cutting or the application of security features that are not found in exactly the same place. In the worst case, this can leads to finding the same number of groups as the number of counterfeits (i.e. each counterfeit will be considered as unique and thus each ‚Äúgroup‚ÄĚ will only contain one unique sample) (Fig. 6).
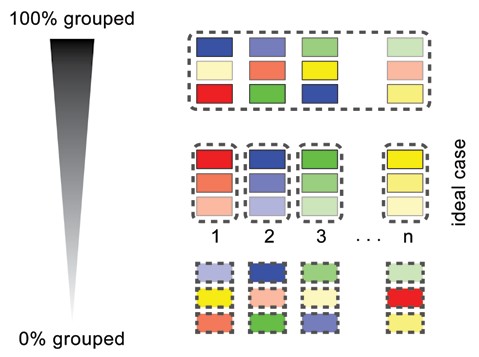
Fig. 6. Illustration of ideal scenario (centre) and two extremes: all counterfeits are wrongly linked in one group (top) and no links were found (bottom).
A practical example of this can be found in the illustration of characteristics related to printing. If the forensic intelligence characteristics are too general, it results in linking all the samples together ‚Äď for example, characteristics such as inkjet printing that was interesting and valuable until inkjet become widely used. The current description of counterfeits as ‚Äúinkjet made‚ÄĚ is of very low value as in Switzerland it links 97 percent of counterfeits. On the contrary, due to the drying of inks in jets, or the defects of the drum in cases of laser printers, counterfeits printed on the same devices can have slightly different characteristics and when too strict criteria is applied they are considered different and thus not originating from one source.
Scenarios for counterfeiting
To resume the possibilities of forensic intelligence, four scenarios (models) will be considered based on counterfeiters using the same source images, technology/materials. In those scenarios, two variables are considered:
- utilisation of the same or different source banknote (image) as template for production of counterfeits
- same or different technology/materials used for production, regardless of whether this was intentionally or unintentionally done (production for a longer period, change of device, refill of cartridges by different inks, etc.)
This leads to four combinations that are ordered in increasing difficulty for the forensic intelligence approach:
1. Same banknote, same technologies/materials
In this scenario, multiple counterfeits are printed from one image of a genuine banknote on one printer. From an intelligence perspective, linking can easily be done according to the characteristics of the genuine banknote used as a source image and through the further evaluation of the physical and chemical properties of the materials that will support the hypothesis regarding the origin of the multiple counterfeits.
2. Same banknote, different technologies/materials
In this scenario, linking can be done as mentioned above as according to the characteristics of the source banknote. Only a physical or chemical examination can lead to a wrong conclusion ‚Äď links will not be found.
3. Different banknotes, same technologies/materials
This scenario is difficult from an intelligence point of view because the characteristics of source banknotes cannot be used, and links based on the physical or chemical properties of printers can be very ‚Äúweak‚ÄĚ with a corresponding increased risk of returning false positives. Moreover, instrumental analysis is more difficult to apply systematically to thousands of counterfeits each year.
4. Different banknotes, different technologies/materials
This scenario is the most difficult because the characteristics of the source banknotes or the device (material) characteristics do not indicate any links. From a document examination perspective, there is nothing to do ‚Äď forensic intelligence analysis relies on information regarding the modus operandi of production (for example, the specific way of imitating holograms or watermarks) or entering counterfeits into circulation. An evaluation of other evidence from different fields of forensic science can be used to prove the same origin (witness statements, CCTV records in shops, fingerprints or DNA on counterfeits etc.).
Ways of reproducing banknotes
In the simplest model considered above (the first scenario), the counterfeiter uses one genuine banknote, scans the recto and produces multiple printouts by printing sheets containing only one image of the note. Afterwards, this is repeated for the verso. The characteristics of the images will be the same on all the printouts. Due to scanning, if any defect or trash marks are present, those characteristics are going to be presented on all printouts as well.
However, in practice various scenarios can occur, from the scanning of multiple notes simultaneously (those defects visible on the first note will not be visible on the second because the placement of the note on the scanner was different) to the ‚Äúcloning‚ÄĚ of the banknote image using graphical software to fully cover any sheet of a particular size. In that case, the characteristics of the image, like the halftone of two notes printed on one sheet, will be different. On the contrary, all counterfeits on same position of sheets are linked by image characteristics.
Current problems of forensic intelligence analysis of counterfeit banknotes
One of underestimated factors that might have a negative impact on the forensic intelligence of banknote counterfeits is the sharing of knowledge and the images found on the Internet, along with the counterfeit deterrence technology installed in devices that can be misused for the production of counterfeits.
1. Sharing of know-how and images on the Internet
An analysis of the Internet indicates that counterfeiters are sharing both know-how and source images. This can have the following impact: counterfeits from two different counterfeiters can have more similar characteristics than would be case if the source images and/or information were not shared.
How should this be handled and how can we distinguish between the counterfeiters that share information and images and those that producing the ‚Äúsame‚ÄĚ counterfeits? For the police, information about the links between those counterfeits can be useful (they are linked due to the same modus operandi, the same types of devices, the same shared images) but at the same time it would be useful to extract information that enables them to classify the counterfeits into groups based on counterfeiters. However, if source images, materials, devices, know-how and modus operandi are the same, from a document analysis point of view there is nothing to differentiate them and enable forming a conclusion on the multiple groups ‚Äď risk of finding wrong links exists (Fig. 7).
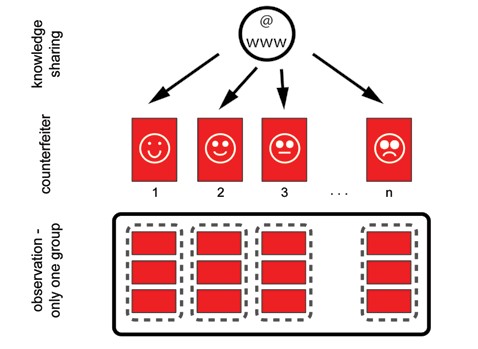
Fig. 7. Impossible to distinguish counterfeits from different counterfeiters.
2. Impact of counterfeit deterence on forensic intelligence
As discussed in the author‚Äôs previous article (BoW ‚ĄĖ 6 (2014)) counterfeit deterrence and tracking systems are one of the ways to eliminate the counterfeiting of currency in the future, but these cannot be considered a universal solution for now and still they have a few limitations:
3. They are not fully implemented in the majority of devices ‚Äď counterfeiters can still find alternatives to the blocked devices
4. The effort to block ‚Äúeverything‚ÄĚ (i.e. software, hardware of printers and scanners) is not effective at least for now.
5. It is focussed more on the prevention of counterfeiting by hobbyists and occasional counterfeiters than on professionals who imitate genuine printing processes (genuine secure offset is imitated by commercial offset).
The implementation of counterfeit deterrence and tracking systems is not without a negative impact ‚Äď it can lead to counterfeiters, upon discovering that devices are not able to copy banknotes, moving to other devices that are not (yet) blocked or it can encourage them to keep old devices in which counterfeit deterrence blockers were not implemented. As discussed above, one of the conditions of effective forensic intelligence is market variability, i.e. each counterfeiter is ‚Äúdoing things‚ÄĚ differently. Not only driven by the choice of a few remaining devices on the market that do not contain counterfeit deterrence protection, but also as supported by exchanges on discussion forums, more counterfeiters are now able to use the same devices and produce similar or even identical results. This can lead to errors of two types: those of the police who are trying to link counterfeits that do not have the same origin (that can lead to long investigations, high cost etc.) and in the worst case they can attribute all the counterfeits produced on one type of device to one counterfeiter in case of expertise for evidential purpose.
6. Other factors influencing effective forensic intelligence analysis
It is apparent that effective counterfeiting intelligence needs to consider all the above and create a system for classification of counterfeits. Moreover, there are other factors to consider: some of them are rather ‚Äúclassical‚ÄĚ problems (for example subjectivity of our decision), some of them are again related to the explosion in the number of counterfeits produced digitally that need to involve more people in police or bank laboratories to classify them. In many countries justice may only observe increasing level of counterfeiting, but it has not a lot of tools to fight it on all levels (legal, political, organizational) with decreasing number of staff. Last but not least, models are different from reality. When modelling reality we can never be sure if our models are adequate and if counterfeiters do not think differently. When working with real counterfeits, we never know ground true ‚Äď if our links are correct or not.
Subjectivity of classification
Subjective description in an increasing number of samples from an increasing number of counterfeiters is more and more difficult. For example, paper is traditionally classified as UV dull or luminescent, but where is the boundary? If counterfeiters would use only two types of the paper, the classification would be easy. In reality, dozens of different papers are used and finding the ‚Äúcutting edge‚ÄĚ where on one side is one type and on the second side is another is difficult. If those comparisons are done by different people using different sources of light (or simply just working in different ambient light conditions) results will vary even more. The acquisition of values by instruments that use numerical values can only be a partial solution, as the decision making needs to be done later in order to find the threshold under which values are in first category and which in. An objective approach can be a solution but creating a definition of the ideal threshold is impossible, especially when considering environmental changes as paper and inks fade out.
Centralization vs. decentralization
Particularly in the case of geographically large countries, due to travelling distances it might be easier to create a central database (maintained by a central laboratory) from multiple local laboratories. This can enhance speed and ‚Äúbring forensics closer to investigators‚ÄĚ, however it is not risk-free ‚Äď the same instruments and procedures should be used to ensure that the same system of classification is used. If this were done in one central laboratory (and by one person), in case of doubt one could return to the previous samples and compare them to the specimen. One should keep in mind that statement associated with computer databases ‚Äúgarbage in, garbage it‚ÄĚ ‚Äď incorrectly completed databases will never serve as intended and can lead to delays in investigation due to the need to revisit the samples and eventually reclassify them.
Models vs. reality
The weakness of all forensic intelligence studies when working with real samples is that ground true is not known. Different authors propose to verify their conclusions (or ‚Äúpersuading the reader that their solution works‚ÄĚ) by comparing their conclusion to the following:
· other physical evidence (fingerprints, DNA)
· other investigative information (surveillance of suspects, eavesdropping, etc.)
· information about seizure of samples (samples seized in the same place, at the same time and from the same counterfeit workshop)
· conclusion (judgement)
All of the above can more or less indicate and confirm the conclusions reached by their chosen approach, but they still have their limits as there is always the risk that only selective information has been used or that incorrect linking has influenced the conclusion (poor judgement).
Conclusion
Digital technologies have completely changed the process of counterfeiting banknotes. Unless all the devices in the possession of the general public are protected by counterfeit deterrence, forensic intelligence will play important role in linking counterfeits and helping to identify large-scale counterfeiters. The above-mentioned aspects should be carefully considered when creating a system for an effective intelligence solution to this problem and while evaluating results of linking.
Need more information on security features and banknote industry, subscribe to the "BANKNOTES OF THE WORLD":
https://www.icpress.ru/en/catalog/currency/detail.php?ID=9262




